The Duality platform enables you to gain new insight from data you could not access previously. Duality enables multiple organizations to collaborate on sensitive data while ensuring that sensitive data is protected.
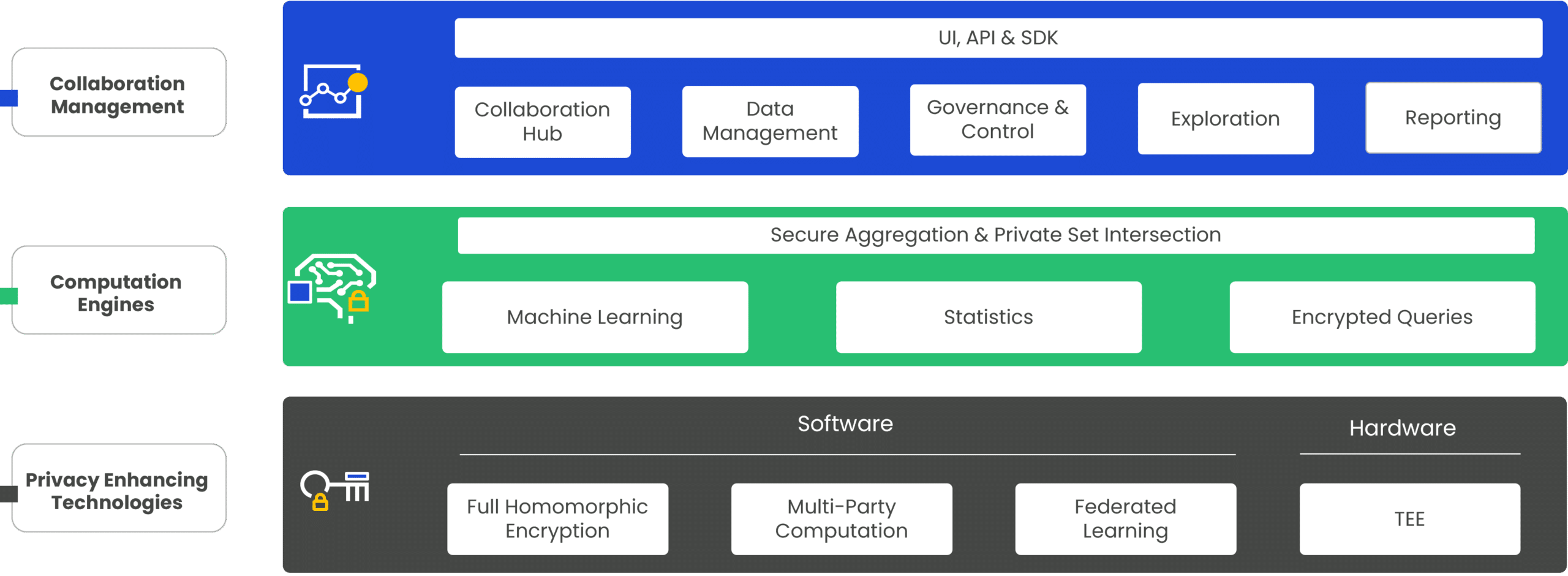
The Duality platform provides end-to-end capabilities to manage the collaboration network and initiate secured computations. This includes the entire data lifecycle, from setting up a secure collaboration network, to data management tools such as data pre-processing and schema alignment, through various data governance mechanisms to reporting.
All computations run in a privacy-preserving manner. The platform enables the option of running aggregated data analysis as well as running a private set interaction between multiple datasets as a step prior to the ML or statistical computation.
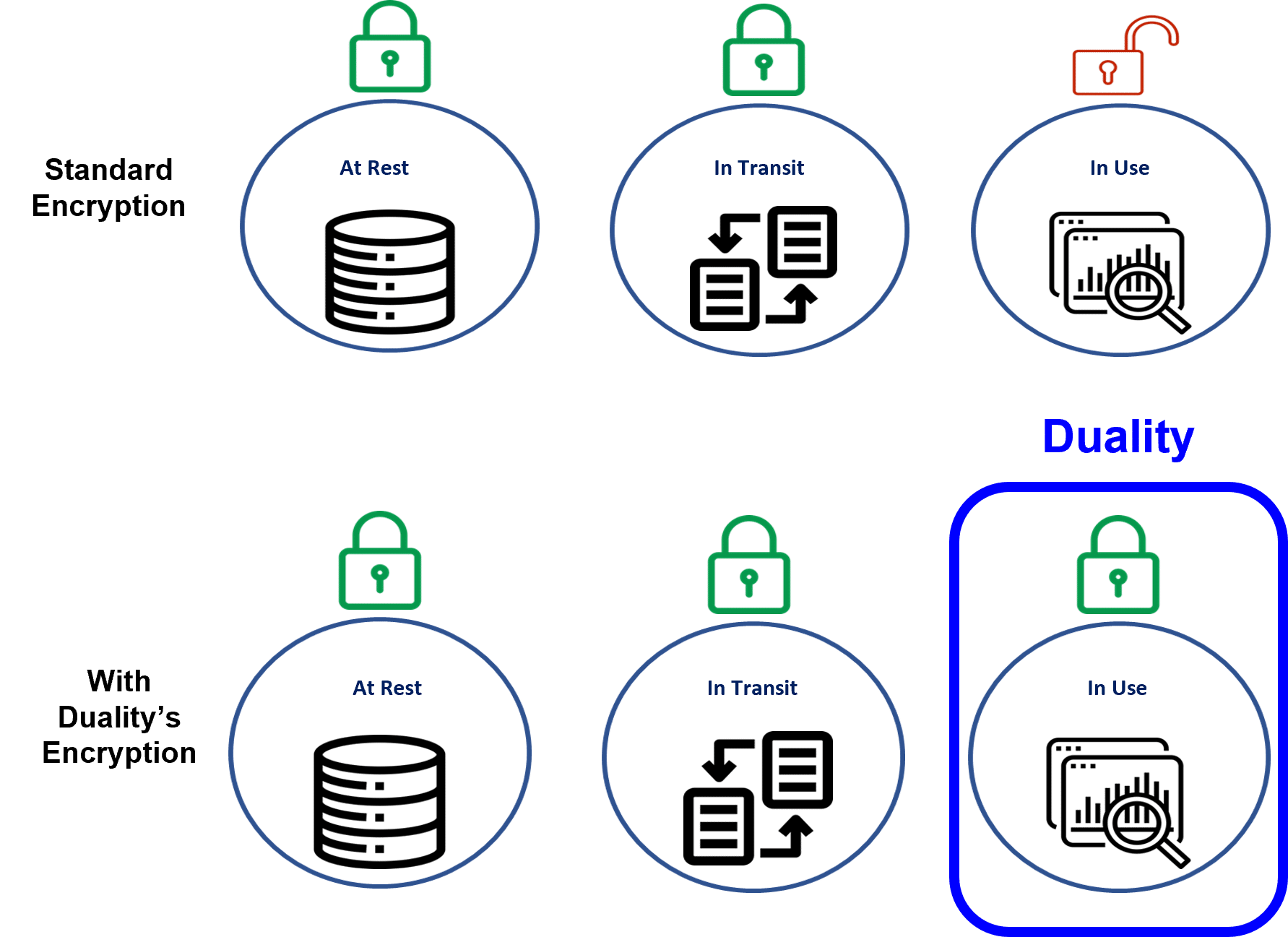
Data has three basic states: at rest, in transit, and in use. Organizations that handle sensitive data such as personally identifiable information (PII) or confidential material typically encrypt or otherwise protect that data while it is being stored (at rest) or when it is being transmitted (in transit). However, when the data is processed, analyzed or manipulated in any way (in use), it must be decrypted – making it visible, vulnerable and at risk. This prevents utilization and monetization of the data.
The Duality platform uses multiple technologies to protect sensitive data. The Duality approach is that one size does not fit all, instead providing the best of breed technology. This enables you to select the most appropriate technology for your use case. For some cases, multiple technologies are combined and used at the same time.
The Duality privacy-preserving data collaboration platform leverages cryptographic methodologies that enhance several Privacy Enhancing Technologies (PETs). PETs allow complex computations on data while the data or model itself are kept hidden and secured during computing. No one PET is optimal for all data collaboration initiatives. The Duality platform therefore combines multiple PETs with cutting-edge data science to provide data governance and privacy.
FHE is a powerful cryptographic primitive that enables performing computations over encrypted data without having to decrypt any data or share access to any secret keys. FHE covers a set of encryption methodologies that allow computations to be performed on encrypted data while it is being used – without ever decrypting it. FHE schemes use a mapping between two mathematical structures that preserves the computational characteristics of the structures. This allows operations to be run directly on encrypted data (ciphertexts), while yielding the same results as if the functions were run on plaintext.
Duality is a prime contributor to the research and development of OpenFHE, an open-source privacy-preserving cryptography library, which is designed for usability and performance, providing simpler APIs, modularity, cross-platform support, and integration of hardware accelerators. OpenFHE complies with the HomomorphicEncryption.org post-quantum security standards for homomorphic encryption. For more info regarding OpenFHE, visit https://www.openfhe.org/.
Multi-party computation, commonly referred as MPC, is a PET technique that utilizes cryptography techniques to allow multiple parties to perform joint computations on individual inputs without revealing the underlying data between them or interim computations.
Federated Learning (FL) is a distributed machine learning (ML) technique that enables model training on data from multiple, decentralized servers with local data samples, without exchanging or moving data. This approach ensures that the data remains in its original location and is not exposed to any other parties.
Another characteristic of FL is that it is typically composed of heterogeneous datasets where the size of the dataset varies from one data owner to another.
Duality developed a second layer of security on top of FL to ensure that the federated computation itself is performed while encrypted, keeping the model concealed from all participants and the computation operation secured.
Trusted Execution Environments (TEEs) provide secure computation capability through a combination of special-purpose hardware and software built to use those hardware features. It provides a mechanism by which a process can run on a processor without its memory or execution state being visible to any other process on the processor, even the operating system or other privileged code.
Other processes (whether local or remote) that must trust an enclave can receive attestation that the enclave is genuine, and that the code running in it and the static parts of its memory space are exactly what is expected. Such attestation is guaranteed using cryptographic capabilities. Duality added the option to use TEE that works in conjunction with the cryptographic solutions. The platform runs on top of AWS nitro enclave and Google confidential space. Azure TEE is in the roadmap.
Maximize the value of sensitive, regulated, or confidential data.